Getting started managing your TR-069 CPEs on Cloud ACS Server
Introduction
Cloud ACS server “DMS” (hereinafter referred to as “DMS”) supports management of subscriber devices by using TR-069 protocol (CWMP).
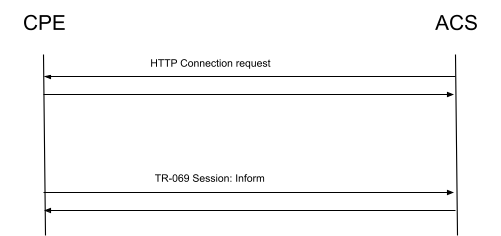
The protocol involves that the CPE initiates work with the management server, that is, the management session begins with a request made from the device.
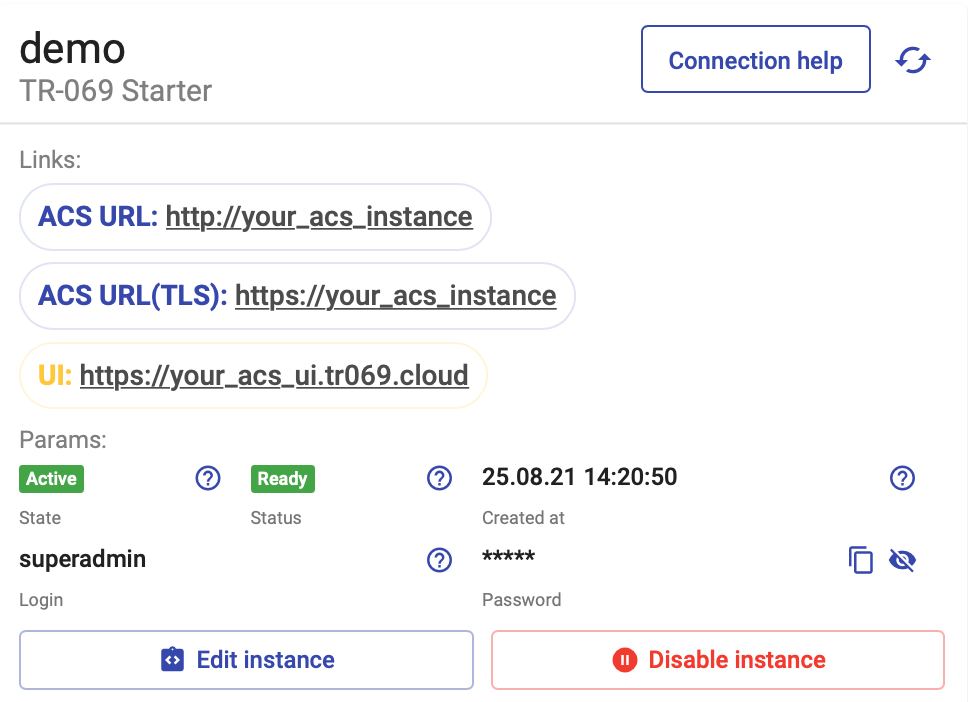
To initiate a TR-069 session with the ACS the CPE needs to know the address of its associated ACS. The ACS address (ACS URL) can be provided to the CPE using various mechanisms, see the information below (Section How to connect your CPE devices to DMS).
If you have already created instance, you can get the ACS URL from Links section:
| ⚠️ Caution |
|---|
| If you try to open the ACS URL through a browser, you will get a "Bad Request" error, this only works for TR-069 messages. |
After successful registration of the CPE on the ACS server, the ACS can also initiate the TR-069 session, by using an HTTP Connection Request Mechanism (CNR), in which the ACS sends an HTTP GET request to the address specified by the device in the Inform message.
How to connect your CPE devices to DMS
If you want to connect a device to DMS, you need to tell it the address of the ACS server. The following options are used to configure the ACS server on the devices already installed on the network:
- You can configure TR-069 settings via the device’s WEB interface or other management protocols (Telnet, SSH).
- You can use OMCI to configure the TR-069 settings interface from the OLT side (GPON).
- You can use a DHCP server: the settings for connecting to TR-069 ACS server are transmitted using the option 43 of DHCP server. While obtaining an IP address, the subscriber device can report that it supports TR-069, in this case the option 60 (DHCPv4) or option 16 (DHCPv6) will contain the substring “dslforum.org”. In response, the DHCP server MAY add the ACS URL to sub option 1 of option 43 (DHCPv4) or option 17 (DHCPv6).
| 📝 Source |
|---|
| See Chapter 3.1 ACS Discovery in BBF TR-069 Amendment 6 |
Example of ISC DHCP configuration:
option space tr069;
option tr069.acs-server code 1 = text;
option tr069.provisioning-code code 2 = text;
subnet 192.168.1.0 netmask 255.255.255.0
{
option routers 192.168.1.1;
range 192.168.1.2 192.168.1.254;
option domain-name-servers 8.8.8.8; vendor-option-space tr069;
option tr069.acs-server "http://your-acs.pro:7547";
}
- You can use a special firmware version, which already has settings for connecting to TR-069 ACS server.
- If none of the above helps, you can contact us and our engineers will try to find the best solution!
Nginx proxy for ACS
In order to replace the ACS server already used in your network or to connect the internal management network to the DMS, you can deploy a Nginx reverse proxy (HTTP reverse proxy) on your network to redirect requests from the CPE to the cloud ACS.
Example of nginx configuration:
upstream acs-upstream {
server <ACS URL of your instance on Cloud DMS>; # (1)
}
server {
listen 7547 default_server;
listen [::]:7547 default_server;
server_name <Proxy name of ACS Server in your network>; # (2)
root /usr/share/nginx/html;
# Load configuration files for the default server block. include /etc/nginx/default.d/*.conf;
location / {
proxy_socket_keepalive on;
proxy_http_version 1.1;
proxy_read_timeout 100;
proxy_send_timeout 100;
proxy_connect_timeout 100;
proxy_set_header Connection "keep-alive";
proxy_set_header Host <Proxy name of ACS Server in your network>; # (3)
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
server_name_in_redirect off;
proxy_pass http://acs-upstream; break;
}
}
server cwmp-test-xyz.acs.tr069.proORserver cwmp-test-xyz.acs.tr069.pro; keepalive 10;server_name proxy_acs_url_in_your_networkproxy_set_header proxy_acs_url_in_your_network
Connecting devices behind NAT
The Connection Request mechanism involves the use of HTTP GET request made from the DMS to CPE. While using this mechanism, a problem arises when the CPE is located behind NAT - the CPE address is not directly accessible from outside the network.
BroadBandForum offers two protocol extensions to address this issue:
- STUN
- XMPP
In cases where a CPE device is behind NAT and does not support any of the BBF suggested NAT traversal solutions, the DMS provides additional alternatives:
- SHORT Periodic Inform Interval(PII)
- Usage of an HTTP Proxy
All possible NAT traversal solutions, except HTTP Proxy, are readily available on all cloud ACS instances by default. No additional actions are required to enable them on your instance.
How does the algorithm ascertain the most optimal management mode for devices that are behind NAT?
DMS ACS considers all options that can be used for management of CPE device behind NAT and choose the best one.
When activating management mode for devices situated behind NAT, the following priority is enforced:
- HTTP Proxy will be used in case when it's configured for cloud ACS instance.
- XMPP will be configured and enabled on CPE device in case when CPE device supports it.
- STUN will be configured and enabled on CPE device in case when CPE device supports it.
- If none of the previously mentioned solutions is supported by the CPE and no HTTP Proxy is configured, DMS ACS configures SHORT PII on the CPE device.
A detailed description of each solution for managing devices behind NAT is provided below.
Solution 1 from BBF: XMPP
| 📝 Source |
|---|
| Described in the document BBF TR-069 Amendment 6 at Annex.K |
The DMS will automatically configure the XMPP server settings when the device connection is established for the first time. If your device doesn't support XMPP or is connected to ACS without NAT, ACS will not provide XMPP specific settings.
In this case, CPE connects to the XMPP server located on the DMS platform and maintains a persistent connection with it. If it is necessary to contact the CPE, the DMS sends a specially formed message (XMPP Connection Request) to the Jabber ID of the CPE. After receiving XMPP CNR and validating it, CPE initiates CWMP session with the DMS.
Solution 2 from BBF: STUN
| 📝 Source |
|---|
| Described in the document BBF TR-069 Amendment 6 at Annex. G |
The DMS will automatically configure the STUN server settings when the device connection is established for the first time. If your device doesn't support UDP Connection Request or is connected to ACS without NAT, ACS will not provide STUN specific settings.
In this option DMS uses a built-in STUN server.
After configuration the devices will periodically send Binding Request messages to the STUN server address and notify ACS of the UDP Connection Request Address in the CWMP Inform message. This allows ACS to trigger the UDP Connection Request mechanism at any time.
Please, also note that in some cases the additional configuration on border network devices may be required to support a large number of UDP sessions (NAT bindings).
Solution 3: HTTP proxy
If your CPE doesn't support XMPP or STUN.
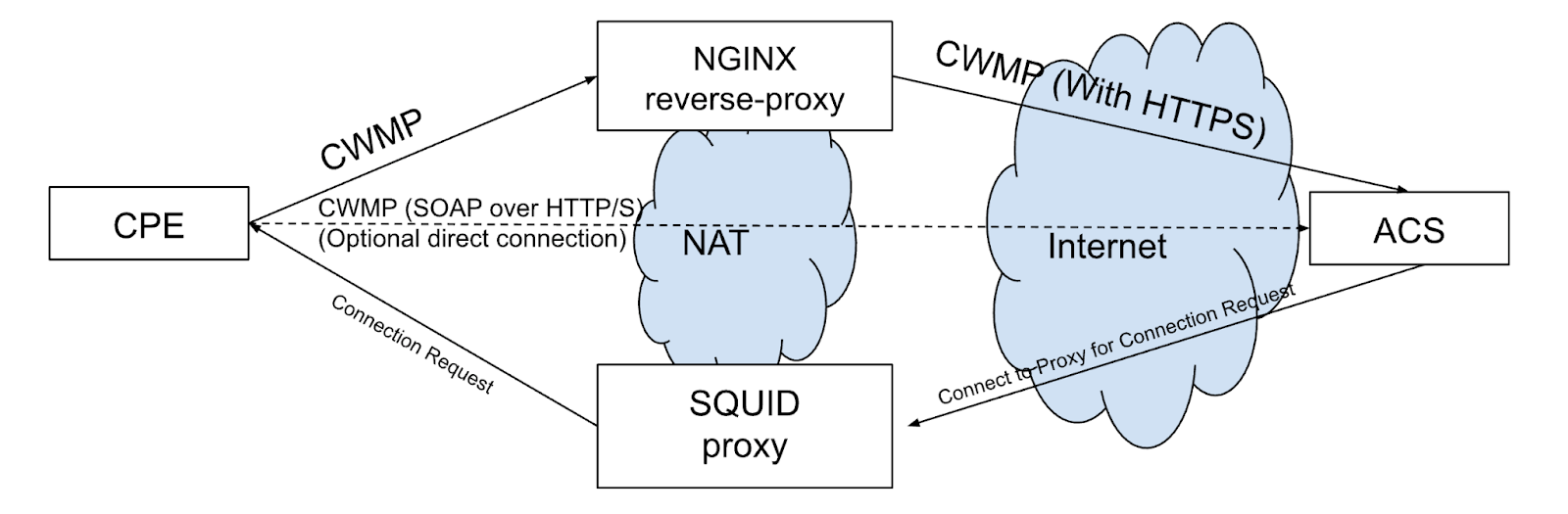
Deploy an HTTP proxy server in your network with direct access to the devices. Connection diagram is shown below. The proxy must be accessible from the Internet (have public IP).
The recommended software for installation as a proxy server is Squid HTTP proxy.
Below is an example of configuration for Squid.
acl localnet src 34.66.233.201 \# cloud dms CNR 1\nacl localnet src 35.222.183.119 \# cloud dms CNR 2
acl SSL_ports port 443
acl Safe_ports port 1025-65535 # all unregistered ports
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localhost manager
http_access deny manager
http_access allow localnet
http_access allow localhost
http_access deny all
http_port 3128
cache_dir ufs /var/spool/squid 4096 32 256
coredump_dir /var/spool/squid
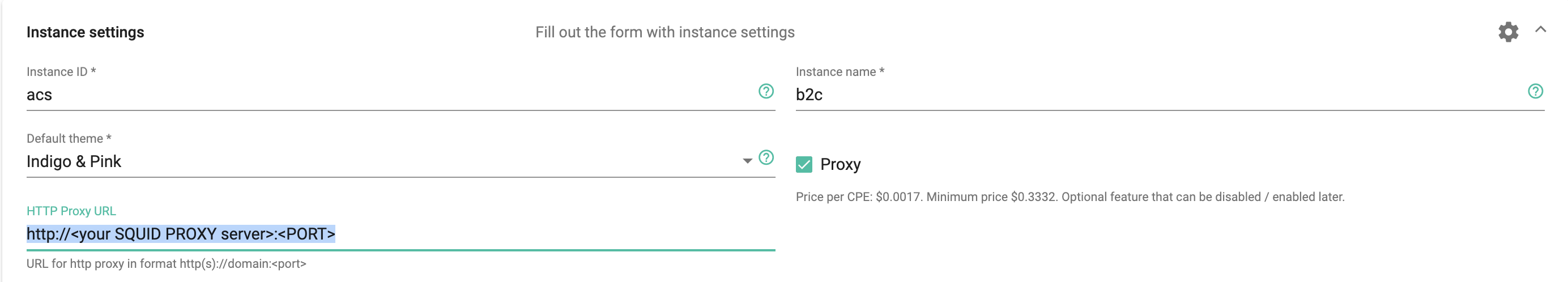
After Squid is installed, specify its IP address and port in proxy field in your DMS instance settings, or contact us, so we can help you set it up correctly.
On your firewall IP Address you should allow ACS CNR Sender: 34.66.233.201, 35.222.183.119.
The second proxy (nginx reverse proxy) on the diagram is optional. It can be used to ensure TLS connection from devices to the DMS, if TLS isn’t supported by the devices. Also, it can be used to proxy requests from CPE devices to cloud ACS instance URL in case when ACS URL has already configured on devices, and you are not able to change it.
Solution 4: SHORT Periodic Inform Interval
When a CPE device does not support any of the listed solutions, DMS ACS automatically detects this scenario and adjusts the SHORT Periodic Inform Interval to 20 seconds. In this configuration, the CPE device communicates with the ACS every 20 seconds, sending a 2 PERIODIC CWMP event code.
To prevent system overload due to a large number of short periodic requests, the full logic for the 2 PERIODIC event is triggered according to the standard Periodic Inform Interval (PII), typically set to 4 hours. Consequently, the state of the CPE device is updated in the ACS. These updates are reflected in the UI of the support portal, admin portal, or when accessing the CPE device object via the NBI interface.
When managing such a device, for instance, executing operations via the support portal, scheduling the execution of mass campaigns, or interacting with the CPE using the NBI interface, DMS ACS will perform all requested actions during the nearest CWMP session.
Common recommendations
When connecting a large number of devices behind NAT, especially if most of them do not support BBF suggested solutions, it is highly recommended to configure the use of a Squid Proxy. This configuration helps reduce the load on both the CPE devices and the DMS ACS by utilizing a short Periodic Inform Interval (PII).